Hacking gets a bad rap. When most people hear the word, they think of malware, identity theft, espionage, and apology emails sent to friends in the embarrassing aftermath of a compromised Facebook account.
Try this: do a Goggle Image search for the word “hacking.” See the skulls, Guy Fawkes masks, padlock icons and the images of green-tinted code lifted straight from the dystopia that is The Matrix. Message received: hacking is very scary.
Google Image Search for the word “hacking.” Scary.
Where does this popular perception come from? For over thirty years, outlaw nerds have hacked on the big screen: TRON and War Games gave us the image of the young rebel hacker skirting heavy security with a few effortless keystrokes, archetypes which evolved into The Girl with the Dragon Tattoo‘s Lisbeth Salander, badass hacker. Even stock espionage and heist films require a team member to bypass any security system by clacking away at a laptop (see the entire Mission: Impossible franchise). Real-world events only perpetuate this hacker-as-criminal image. Cindy Cohn, Legal Director for the trailblazing Electronic Frontier Foundation, argues that the Bradley Manning WikiLeaks case is part of a prosecutorial trend toward exploiting irrational fears about computers:
The decision today continues a trend of government prosecutions that use familiarity with digital tools and knowledge of computers as a scare tactic and a basis for obtaining grossly disproportionate and unfair punishments. Let’s call this the “hacker madness” strategy. Using it, the prosecution portrays actions taken by someone using a computer as more dangerous or scary than they actually are by highlighting the digital tools used to a nontechnical or even technophobic judge.
So: hackers are lone, outlaw agitators who use technology as a weapon. And because most of us use our computers like we use our cars—we know enough to make them run, but not enough to understand how they work—hackers seem dangerous for what we imagine they can do with their unchecked powers. Right? Not exactly. First of all, this is a narrow definition of hacking, as computer intrusions like these are typically labeled cracking. Second, they have little to do with the Hacker Ethic formulated at MIT in the 1950s and 60s. Journalist Steven Levy, in his 1984 history of the rise of hacker culture, describes the Hacker Ethic this way:
Access to computers—and anything that might teach you something about the way the world works—should be unlimited and total. Always yield to the hands-on imperative! Hackers believe that essential lessons can be learned about…the world from taking things apart, seeing how they work, and using this knowledge to create new and even more interesting things.
Just a few decades ago, hacking wasn’t about computer code–it was a code of conduct. The Hacker Ethic promoted access in the service of curiosity and invention. In 2013, however, this starry-eyed manifesto seems romantic, or worse, naive. Artistic appropriation, a pillar of Modern Art for over a century, is now prosecuted as plagiarism. Patent Trolls aggressively abuse the patent system for profit, stifling innovation. Benevolent hackers, like the late Aaron Swartz, who believe in ethical disclosure, are persecuted as criminals.
We need to reinvent our cultural imagination of the hacker. Being a student of history, I propose we start looking further into the annals of the past, all the way back to the Renaissance, to find our hacker forebears. Four centuries ago, information was as tightly guarded by intellectuals and their wealthy patrons as it is today. But a few episodes around 1600 confirm that the Hacker Ethic and its attendant emphasis on open-source information and a “hands-on imperative” was around long before computers hit the scene. First, there was Galileo.
Galileo and the Telescope
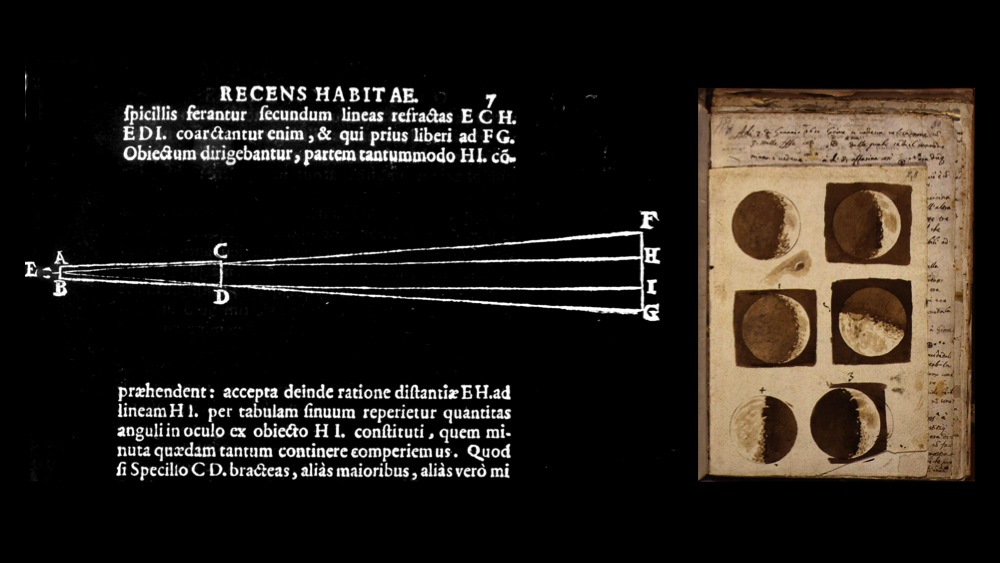
Galileo, Sidereus Nuncias, 1610
OK, so Galileo didn’t invent the telescope. That honor goes to Dutch spectacle maker Hans Lippershey. In 1608, Lippershey applied for a patent for a device “for seeing things far away as if they were nearby.” Although denied based on other concurrent patent claims, the application was notable enough to warrant brief mention in a diplomatic publication announcing new relations between The Netherlands and the Kingdom of Siam. Inspired, scientists tested their own telescope inventions based solely on the description of a “Dutch Perspective Glass.”
In 1610, Galileo published Sidereus Nuncius (The Starry Messenger), describing his telescope and observations of the Moon. Simultaneously, other continental astronomers hurried to make telescopes and point them at the heavens. If Lippershey’s patent had been granted, or if the Dutch had decided to omit this tiny announcement of the application, the history of science might have been different. Perhaps Galileo would have been a minor figure in science; another heretic with crazy ideas. Or the Dutch might have had a head-start on astronomy, physics, and warfare. The public disclosure of the telescope, however vague, literally moved the Earth, yielding proof of the heliocentric model of the heavens.
Tycho Brahe, Johannes Kepler, and the Rudolphine Tables
In the mid 1500s, stellar and planetary data were woefully inaccurate. When Tycho Brahe undertook a serious, from-scratch measurement of the nighttime sky, he was the first to do so in almost 300 years. So it was understandable he was incredibly protective of his data. However, Brahe entrusted his student, Johannes Kepler, with the completion of new star charts for publication–and twenty-six years after Brahe’s death, Kepler published them, calling them the Rudolphine Tables. Instead of a sequence of dates with corresponding planetary positions, Kepler’s tables performed more like a computer. Using the provided formulas and instructive examples, users could calculate future planetary positions.
Kepler (left), Brahe (right), and The Rudolphine Tables, the original open-source program.
These tables are an open source tool, perhaps the very first. The data–and formulas required to convert it into astronomical information—empowered scientists to pursue their own research and observations. Pierre Gassendi used the tables to predict a transit of Mars in 1631, and in 1639, Jeremiah Horrox predicted a transit of Venus. Kepler’s data was for the benefit of science, not personal profit.
La Perspective Curieuse
You’ve probably seen those street-art illusions where a sidewalk chalk drawing looks three-dimensional when viewed from a specific angle. The technique is called anamorphosis, and it dates back to the Renaissance. Hans Holbein famously used the effect in his painting, The Ambassadors (1533), where the enigmatic blob in the foreground is revealed as a skull only to viewers standing in the correct position.
Hans Holbein’s painting, The Ambassadors, with its anamorphic skull.
The illusion was used to amaze, but it was also a useful technique for concealing sensitive material. For over 150 years, anamorphosis was used as a secret code to protect dissenting political messages, unpopular religious ideas, and even taboo sexual imagery. Until Jean François Niceron gave it all away.
A talented mathematician and artist, Niceron revealed for the first time the geometry behind the illusion. Already renowned for his illusions of sacred figures in churches, Niceron published La Perspective Curieuse(The Curious Perspective) in 1638. On top of explaining the technique, Niceron actually illustrated himself in the act of making his most famous illusions. He was a magician who revealed his own tricks–so that we could all do magic.
Jean François Niceron depicting himself in the act of drawing an anamorphic image, from La Perspective Curieuse.
Edward Wright
Ever wonder why the Mercator World Map hangs in every classroom despite its egregious distortions of scale? Well, its significance isn’t about land area. It’s about navigation. The cylindrical projection method that Gerardus Mercator introduced in 1569 flattened the earth into parallel meridians, giving sailors regular and measurable reference markers for straight-line routes across the oceans. The map saved lives. Not surprisingly, its importance—and monetary value—motivated Mercator to keep his projection formula secret.
Until Edward Wright hacked it. And improved it. And, like a true hacker, published the formula. His 1599 publication of Certaine Errors in Navigation broke Mercator’s cartographic monopoly.
Edward Wright, Certaine Errors in Navigation, 1599. Frontispiece (left), and his more precise cylindrical projection map of the world (right).
Traveling to the Azores in 1589 under orders from Elizabeth I, Wright broke Mercator’s code with practical, hands-on experience at sea. Combined with his mathematical training, he produced tables with data and instructions for constructing a more accurate cylindrical projection. More than a new, more accurate map,Certaine Errors in Navigation was—like Kepler’s Rudolphine Tables—a computer for producing your own map. Wright’s hack gifted sailors with abilities beyond sea-borne experience. Instead of Mercator’s consumers, they were now self-sufficient cartographers at sea.
Edward Wright’s planisphere aided sailors in constructing their own cylindrical projection maps.
Wright understood the Hacker Ethic’s hands-on imperative, to the benefit of all who used his tools. He reminisces in the preface to Certaine Errors that through the expedition he “was first moved… to divert my mathematical studies from theoretical speculation in the Universitie [sic], to the practical demonstration of the use of navigation.” To wit, Wright went from thinker to hacker.
Edward Wright reverse engineered, improved, and shared a secret code. You may not have heard of him before, but he is one of history’s great hackers; a perfect embodiment of the Hacker Ethic.
Between Renaissance and Revolution
Before Galileo, Kepler, Wright, Niceron and others, discoveries and inventions were kept secret. Protection of new insights was regulated through coded publications, legible only to invited insiders. The very idea of peer-reviewed publishing—a cornerstone of academia today—didn’t exist until 1665, with the launch of the Philosophical Transactions of the Royal Society.
The innovators of 1600 were hackers before the word existed; they proposed open sharing of ideas for the benefit of humanity. Isaac Newton, Robert Hooke, Descartes, and the other scientists of the late 1600s could not have inaugurated the greatest scientific innovation of all time—the invention of modern science itself—without the Hackers of the 1600s. The Renaissance’s secretive structure was hacked, and it inspired the Scientific Revolution.
Hacking is a good thing. Hackers ensure we don’t sit still with what we have; they know there’s always more to discover. They extract kinetic energy from the inertia of achievement. We risk stifling discovery when we claim absolute ownership of ideas. We risk our future when we aggressively guard what we believe, often falsely, to be ours. And we risk everything when we persecute the curious and inventive, labeling them as criminals. Let’s restore hacking to its proper place: as a noble tradition dating back hundreds of years, one which kickstarted our modern world. Who knows what wondrous revolution awaits if we just get hacking?
* * * * *